by ezs | Jan 13, 2024 | evilzenscientist
This turned out to be really simple; and there are some really good tools and docs at https://dmarcian.com/
- set up DKIM DNS records
- CNAME selector1._domainkey –> selector1-{domain}._domainkey.{office365domain}.onmicrosoft.com
- CNAME selector2._domainkey –> selector2-{domain}._domainkey.{office365domain}.onmicrosoft.com
- set up DMARC DNS records
- TXT _dmarc –> correct DMARC policy
Then enable DKIM signing in the Defender portal https://security.microsoft.com
Email and Collaboration –> Policies and Rules –> Threat Policies –> Email Authentication settings
- select the domain, click on “sign messages for this domain with DKIM signatures”
It might take a while for the DNS records to propagate.
Finally test the DMARC and DKIM settings, I used the DMARC Record Checker https://dmarcian.com/domain-checker
If you end up looking to use DMARC reporting, and sending to a third party/alternate domain – you also need to set up DNS records in the receiving domain:
- set up External Domain Verification (EDV) records in DNS
- TXT {domain}._report._dmarc –> v=DMARC1
by ezs | Dec 24, 2023 | evilzenscientist
Note so I can find it next time:
storcli64 /c0 set alarm=silence
Docs here
by ezs | Nov 28, 2023 | evilzenscientist
If you’ve worked with Azure for any real length of time, there are limitations to what is stored in the Azure Activity Log – both in terms of content and retention.
The solution is to send Azure logs to a Log Analytics Workspace, and retain that for as long as you needed.
Today I needed to dig into an event that occured back in the summer, featuring Bastion. A simple Kusto query with the date range and searchable text got me results in a few moments. Some display filtering of the correct columns got me to a happy place.
// Log Analyics query
search “BastionHost” // search is case-insensitive
| where TimeGenerated between (datetime(2023-06-01) .. datetime(2023-06-15)) // date ranges
| project TimeGenerated, Caller, CorrelationId, SubscriptionId, ResourceGroup, OperationNameValue, Properties_d.resource, ActivityStatusValue
// just show the columns we care about (comment the entire line if you want all)
by ezs | Oct 17, 2023 | evilzenscientist
Zoom have deprecated their JWT authentication against the backend API, and moved to OAuth.
Happily – Joseph McEvoy has updated the PSZoom module for PowerShell – and it’s working just great.
Create a new Server-to-Server OAuth through the Zoom App Marketplace, and you’re set:
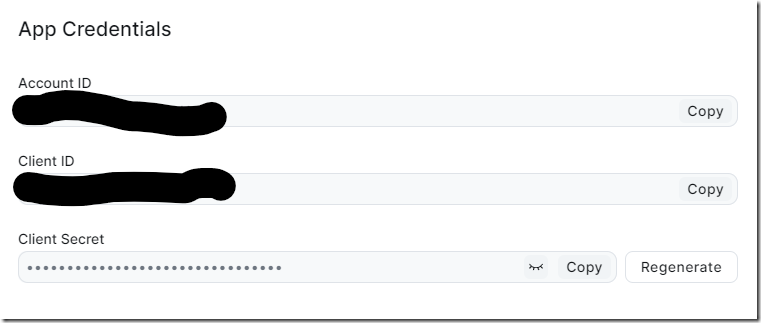
Your usage will vary, but there is a really nice role based model (or “Scope”) for the API – I gave this just read access to meetings – and it’s been fine.
import-module PSZoom
# get the values from the Zoom Marketplace
# Develop –> Build App –> Server-to-Server OAuth
$AccID = ‘from Zoom’
$ClientID = ‘from Zoom’
$ClientSecret = ‘from Zoom’
Connect-PSZoom -AccountID $AccID -ClientID $ClientID -ClientSecret $ClientSecret
$MeetingID = ‘meetingID’
$ZoomRegistrants = Get-ZoomMeetingRegistrants $MeetingID -pagesize 300
$reghashtable = $zoomregistrants.registrants
write-host $reghashtable.count
$outputs = $reghashtable |foreach-object {
return [pscustomobject]@{
fname = “$($_.first_name)”
lname = “$($_.last_name)”
email = “$($_.email)”
regtime = “$($_.create_time)”
}
}
$outputs | sort-object regtime | export-csv “zoom-meeting.csv” -notypeinformation
by ezs | Oct 17, 2023 | evilzenscientist
Here is a header
Some text that’s easy.
Tinkering with Markdown
I’m looking at using Markdown to write posts.
by ezs | Jul 22, 2023 | evilzenscientist
Well – I thought the bad practice of not hashing passwords was behind us, but no, today another example popped up.
If you want a primer on password hashing – take a read of this from Troy Hunt (of Have I been pwned fame).
Short version – hashing is a one-way mathematical function that for an input, always produces the same output. It’s best practice to store passwords for websites as a hashed value (or hash+salt to be honest) – so in the event that the site database is compromised, there’s a list of usernames or emails, but no passwords. It also means that you can’t get back to your old password – so you should never see a “mail me my password” or get emails saying “here is your username and password”.
So, back to the school district. Their jobs page has a “create account” link, which lets you do the email address and password thing.


So far, so good. At login – there is the usual credentials page. But what’s that? A “Send Password” button.
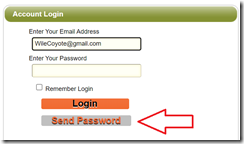
And, as you’ve guessed, it sends back a cleartext password, to the email account used to sign up.
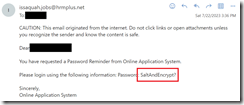
Behind all of this are job applications, and also PII including resume, certification information, disclosures, address and phone numbers.
So what now?
The diligent thing is to contact someone, a Data Registrar, a Web Master – anyone really.
That’s going to be in the next blog post.
by ezs | Jul 1, 2023 | evilzenscientist
As we keep seeing – Azure tag names are not case-sensitive, until they are.
Per the documentation https://learn.microsoft.com/en-us/azure/azure-resource-manager/management/tag-resources
Tag names are case-insensitive for operations. A tag with a tag name, regardless of the casing, is updated or retrieved. However, the resource provider might keep the casing you provide for the tag name. You’ll see that casing in cost reports.
Tag values are case-sensitive.
Per the now four year old bug, Azure Resource Manager itself should respect this (i.e. case insensitive and case preserving) https://github.com/Azure/azure-powershell/issues/9271
Then we get issues with:
CostCenter, Costcenter, costcenter – all being different depending on the tooling in use.
by ezs | Jun 24, 2023 | evilzenscientist
Released back in May, this looks to be stable.
Update is (again) super clean:
zypper migration
select the migration target (i.e. SLES 15 SP5), approve the EULA, wait a while.
I’ve been flagging the ease of upgrade for several years. SUSE have this nailed.
Update: except Redis got a tad confused. Needed to get it re-setup to start correctly.
Update again: openSUSE build server saves the day again: Install package openSUSE:Backports:SLE-15-SP5 / php8-redis along with https://citizix.com/how-to-install-configure-redis-6-on-opensuse-leap-15-3
by ezs | Jun 1, 2023 | evilzenscientist
Another one, again demonstrating the use of extend and mv-expand to pull out the multi-valued array.
resources
| join kind=leftouter (ResourceContainers | where type==’microsoft.resources/subscriptions’ | project SubName=name, subscriptionId) on subscriptionId
| where type == “microsoft.network/virtualnetworks”
| extend vnetCount =array_length(properties.addressSpace.addressPrefixes)
| mv-expand vnet = properties.addressSpace.addressPrefixes
| project SubName, resourceGroup, name, vnetCount, vnet
| order by tostring(vnet) asc
by ezs | Jun 1, 2023 | evilzenscientist
Lots of hygiene work, including cleaning up Azure Action Groups that send to individual emails. That’s a red flag and anti pattern.
Here’s the KQL to read the Action Groups, their subscriptions, and expand out the recipients.
It’s easy work to continue to audit this, and clean up the dead wood.
resources
| join kind=leftouter (ResourceContainers | where type==’microsoft.resources/subscriptions’ | project SubName=name, subscriptionId) on subscriptionId
| where type == “microsoft.insights/actiongroups”
| extend emailRecsCount =array_length(properties.emailReceivers)
| mv-expand emailRecs = properties.emailReceivers
| project SubName, resourceGroup, name, emailRecsCount, emailRecs.name, emailRecs.status, emailRecs.emailAddress
| order by [‘name’] asc






Recent Comments